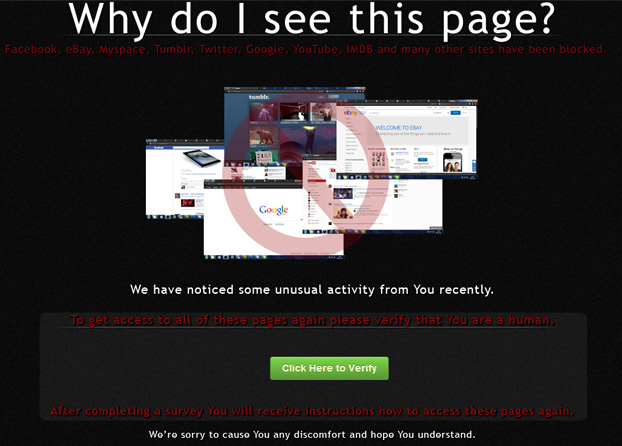
It's pretty scary when your computer displays fake
Metropolitan Police or
Police Central e-crime Unit warnings instead of your favorite desktop theme. These scams are still heavily distributed via infected websites and spam. There are even more ransowmare scams and they all have one thing in common - Ukash. Don't get me wrong,
Ukash is a legit company, it's just that scammers use this service to withdraw money. Ukash logo appears on pretty much every ransowmare warning, no wonder why people started to call it the Ukash virus. As you may know, the most recent examples are the law enforcement variants, mostly the FBI virus and Met Police virus.
Ransomware locks the screen of the infected computer, displaying a message purportedly from your local police department claiming that police officers have found illegal content on the computer and will certainly press charges unless of course you will pay the "fine", usually it's $300 or more. However, since it's a scam you shouldn't pay the so-called fine. Besides, there's not guarantee that you will regain control of your computer even if you pay the fine. Law enforcement agencies strongly recommend that you do not pay the fine and report the crime immediately.
Did you know that the first know version of
ransomware appeared in 1989? Cool, isn't it? It was DOS program that required installation from a diskette that replaced the autoexec.bat file with a new one that counted the number of times a computer was rebooted and when the count reached 90 encrypted all the files on the computer making it unusable until the ransom was paid. The encryption algorithm was quite simple so it was easy to crack and defeat the virus. It's actually amazing to see that things work almost the same way nowadays as well as they did 30 years ago.
The next generation of ransomware showed up around 2005 in the form of cryptoware that started using public and private keys to encrypt the files on the infected computers. By the end of 2006 these ransomware programs started using even more sophisticated
RSA encryption algorithm using longer encryption keys. None of these, however, used Ukash as a payment gateway.
First detected in 2011, Ukash virus is the most sophisticated and hardest to defeat virus of its kind. It uses a "drive-by download" method to infect computers. This means that you don't even have to click or download anything to become infected. All you have to do is visit an infected site. And we all know that scammers mostly tend to infect adult or warez sites, but the virus can be injected from any site so even if you practice safe surfing you can become infected.
Once you are infected, the virus freezes your screen and encrypts your files making your computer unusable. NOTE: not all variants of Ukash virus encrypt files. Usually, the screen is frozen to resemble a message from the FBI or another agency accusing you of committing a crime ranging from illegal copyrighted downloads to having illegal adult content stored on your computer. The virus captures your IP address and displays it the fake warning message and some particularly vicious versions will display a picture containing nudity or some other form of illegal adult content that they claim was found on your computer. Some versions even turn on your webcam and claim that they are monitoring you until you pay the fine. Remember, you have 48 hours to do that, hehe :)
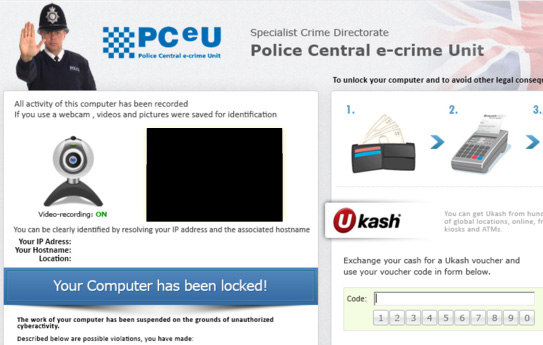
The bottom line though is that if you use some common sense and have a basic understanding of our judiciary system you will quickly realize that this is a scam. If you are doing something illegal with your computer and the FBI or Met Police find out about it they will be knocking on your door with a search warrant, not sending pop up messages and locking your computer. Things like illegal adult material in general, and copyrighted files in particular usually carry prison terms and the FBI are not going to let you off the hook with a such a silly fine for these activities.
The presence of threats like this Ukash virus scam should make people realize the importance of backing up important files, so that they won't be lost once your computer is infected. You should also have real time malware detection installed on your computer to stop the virus from infecting your computer should you visit an infected site. But remember for this to be effective you must update it file every day, since the threats change daily. Most antivirus programs do this automatically each day.
If locking your screen and encrypting all your important files isn't bad enough the latest versions of the Ukash virus piggyback other Trojans to track keystrokes, capture usernames and passwords, etc. Additionally, installed malware may even scan your hard drive for personal information like bank account numbers and social security numbers and transmit this information back to cyber crooks.
Once the virus has encrypted your files there is little you can do to recover those files. This is why you should be diligent in keeping backups of these files on a removable media.
It is highly recommended that you take the infected computer to an expert to ensure that the virus and all associated malware is completely removed from your computer. Some versions of this virus can rebuild themselves if they are not completely removed.
Here are some things you can try if you want to remove it yourself:
The first thing you should try is to restart the computer and start tapping the F8 key to reboot into Windows safe mode with command prompt. Then simply follow the removal instructions below.
Some later versions won't let you start the system in safe mode. If that is the case you will have to create a bootable CD or flash drive using another computer. Again, detailed instructions are give below.
All in all, tt can be so difficult to stay ahead of the criminals, so the best defense is to backup your files regularly, install the latest updates for programs like Java and Adobe because they are continuously identifying and fixing vulnerabilities. Many antivirus packages can scan sites in advance and tell you explicitly that the site is safe, so you might want to consider only visiting sites that have been declared safe by your antivirus program.
Please follow the steps in the removal, guide below to remove Ukash virus from your computer.
Do you have any additional information or questions on this virus? Post your comment or question below. Good luck and be safe online!
Written by
Michael Kaur, http://deletemalware.blogspot.com
Method 1: Ukash virus removal instructions using System Restore in Safe Mode with Command Prompt:1.
Unplug your network cable and manually turn your computer off. Reboot your computer is "Safe Mode with Command Prompt". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Command Prompt" and press Enter key.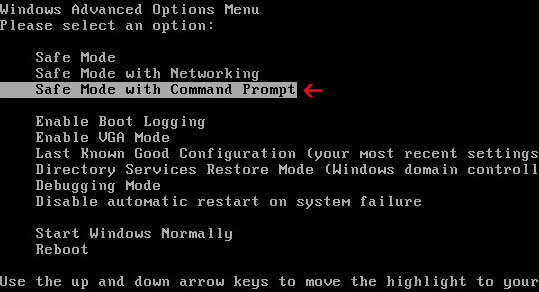
2. Make sure you log in to an account with administrative privileges (login as admin).
3. Once the Command Prompt appears you have few seconds to type in
explorer and hit Enter. If you fail to do it within 2-3 seconds, the virus will take over and will not let you type anymore.
4. If you managed to bring up Windows Explorer you can now browse into:
- Win XP: C:\windows\system32\restore\rstrui.exe and press Enter
- Win Vista/Seven: C:\windows\system32\rstrui.exe and press Enter
5. Follow the steps to restore your computer into an earlier day.
6. Download recommended
anti-malware software (direct download) and run a full system scan to remove the remnants of this virus.
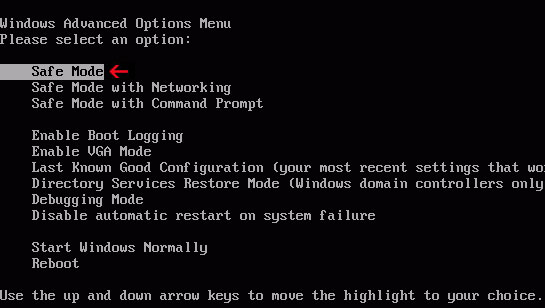
Method 2: Ukash virus removal instructions using System Restore in Safe Mode:1. Power off and restart your computer. As the computer is booting tap the "
F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "
Safe Mode" and press Enter key.
NOTE:
Login as the same user you were previously logged in with in the normal Windows mode.
2. Once in there, go to
Start menu and search for "
system restore". Or you can browse into the Windows Restore folder and run System Restore utility from there:
- Win XP: C:\windows\system32\restore\rstrui.exe double-click or press Enter
- Win Vista/7/8: C:\windows\system32\rstrui.exe double-click or press Enter
3. Select
Restore to an earlier time or
Restore system files... and continue until you get into the System Restore utility.
4. Select a restore point from well before the Ukash virus appeared, two weeks should be enough.
5. Restore it. Please note, it can take a long time, so be patient.
6. Once restored, restart your computer and hopefully this time you will be able to login (Start Windows normally).
7. At this point, download recommended
anti-malware software (direct download) and run a full system scan to remove the this virus.
Method 3: Ukash virus removal instructions using MSConfig in Safe Mode:1. Power off and restart your computer. As the computer is booting tap the "
F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "
Safe Mode" and press Enter key.

NOTE:
Login as the same user you were previously logged in with in the normal Windows mode.
2. Once in there, go to
Start menu and search for "
msconfig". Launch the application. If you're using Windows XP, go to
Start then select
Run.... Type in "
msconfig" and click OK.
3. Select
Startup tab. Expand
Command column and look for a startup entry that launches randomly named file from %AppData% or %Temp% folders using rundll32.exe. See example below:
C:\Windows\System32\rundll32.exe C:\Users\username\appdata\local\temp\regepqzf.dll,H1N14. Disable the malicious entry and click OK to save changes.
5. Restart your computer. This time Start Windows normally. Hopefully, you won't be prompted with a fake Ukash virus warnings.
6. Finally, download recommended
anti-malware software (direct download) and run a full system scan to remove the virus.
Method 4: Ukash virus removal instructions in Safe Mode with Command Prompt (requires registry editing):1. Reboot your computer is "
Safe Mode with Command Prompt". As the computer is booting tap the "
F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "
Safe Mode with Command Prompt" and press Enter key. Login as the same user you were previously logged in with in the normal Windows mode.

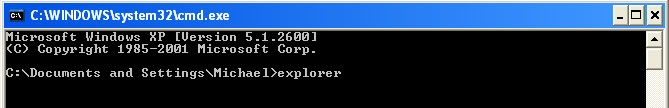
2. When Windows loads, the Windows command prompt will show up as show in the image below. At the command prompt, type
explorer, and press Enter. Windows Explorer opens. Do not close it.
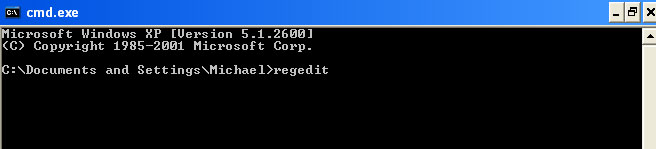
3. Then open the Registry editor using the same Windows command prompt. Type
regedit and press Enter. The Registry Editor opens.
4. Locate the following registry entry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\In the righthand pane select the registry key named
Shell. Right click on this registry key and choose
Modify.
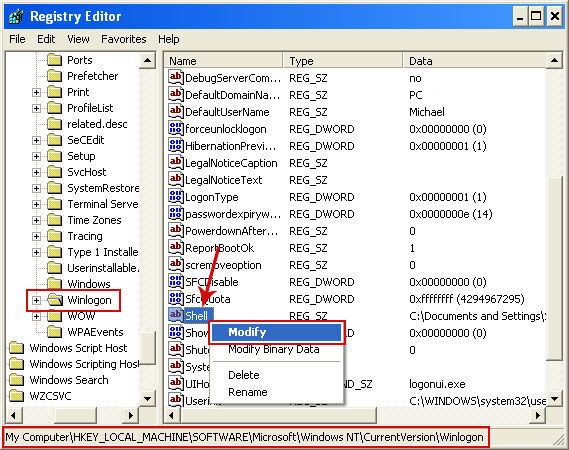
Default value is
Explorer.exe.
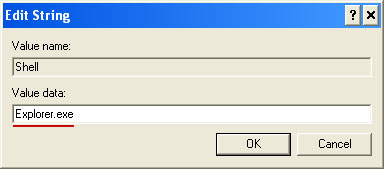
Modified value data points to Trojan Ransomware executable file.
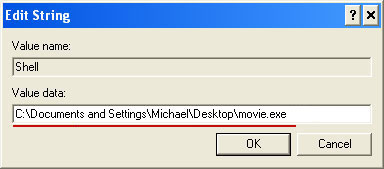
Please copy the location of the executable file it points to into Notepad or otherwise note it and then change value data to
Explorer.exe. Click OK to save your changes and exit the Registry editor.
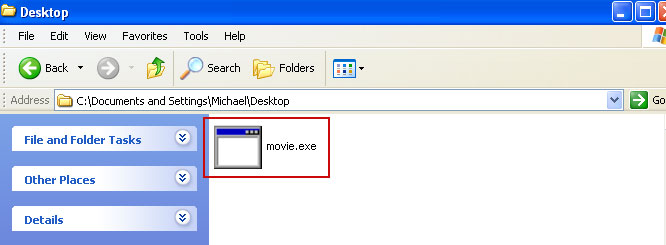
5. Remove the malicous file. Use the file location you saved into Notepad or otherwise noted in step in previous step. In our case, Ukash virus was run from the Desktop. There was a file called
movie.exe.
Full path: C:\Documents and Settings\Michael\Desktop\movie.exe
Go back into "
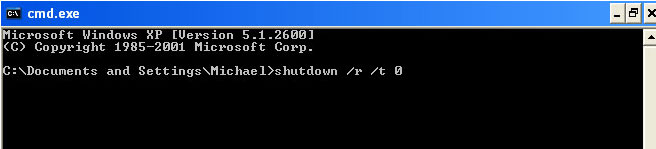
Normal Mode". To restart your computer, at the command prompt, type
shutdown /r /t 0 and press
Enter.
6. Download recommended
anti-malware software (direct download) and run a full system scan to remove the leftovers of this virus from your computer. That's it!
Method 5: Ukash virus removal using Kaspersky Rescue Disk:1. Download the
Kaspersky Rescue Disk iso image from the Kaspersky Lab server. (
Direct download link)
Please note that this is a large downloaded, so please be patient while it downloads.
2. Record the Kaspersky Rescue Disk iso image to a CD/DVD. You can use any CD/DVD record software you like. If you don't have any, please download and install
ImgBurn. Small download, great software. You won't regret it, we promise.
For demonstration purposes we will use ImgBurn.
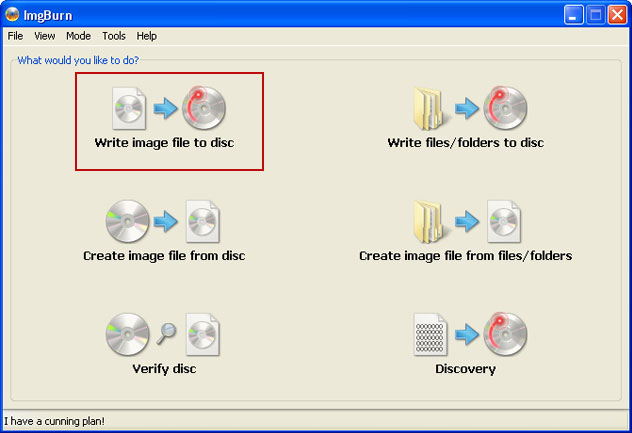
So, open up ImgBurn and choose
Write image file to disc.
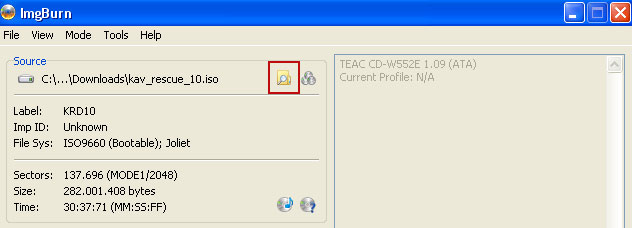
Click on the small
Browse for file icon as show in the image. Browse into your download folder and select
kav_rescue_10.iso as your source file.
OK, so know we are ready to burn the .iso file. Simply click the
Write image file to disc button below and after a few minutes you will have a bootable Kaspersky Rescue Disk 10.
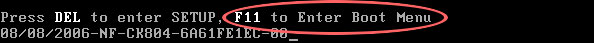
3. Configure your computer to boot from CD/DVD. Use the
Delete or
F2,
F11 keys, to load the
BIOS menu. Normally, the information how to enter the BIOS menu is displayed on the screen at the start of the OS boot.
The keys F1, F8, F10, F12 might be used for some motherboards, as well as the following key combinations:
- Ctrl+Esc
- Ctrl+Ins
- Ctrl+Alt
- Ctrl+Alt+Esc
- Ctrl+Alt+Enter
- Ctrl+Alt+Del
- Ctrl+Alt+Ins
- Ctrl+Alt+S
If you can enter
Boot Menu directly then simply select your CD/DVD-ROM as your
1st boot device.
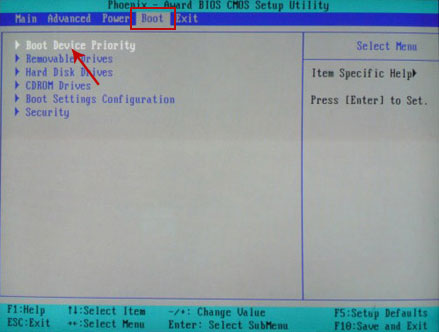
If you can't enter Boot Menu directly then simply use
Delete key to enter
BIOS menu. Select
Boot from the main BIOS menu and then select
Boot Device Priority.
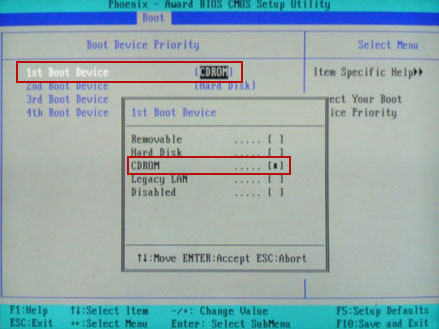
Set CD/DVD-ROM as your
1st Boot Device. Save changes and exist BIOS menu.
4. Let's boot your computer from Kaspersky Rescue Disk.
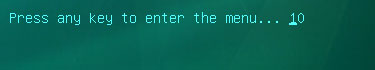
Restart your computer. After restart, a message will appear on the screen:
Press any key to enter the menu. So, press
Enter or any other key to load the Kaspersky Rescue Disk.
5. Select your language and press
Enter to continue.

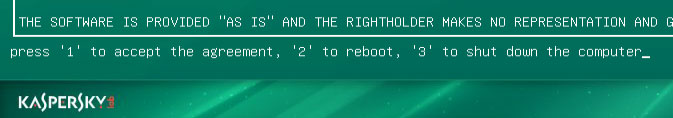
6. Press
1 to accept the End User License Agreement.
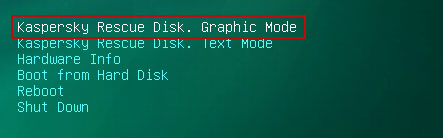
7. Select
Kaspersky Rescue Disk. Graphic Mode as your startup method. Press
Enter. Once the actions described above have been performed, the operating system starts.
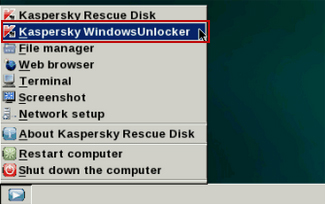
8. Click on the
Start button located in the left bottom corner of the screen. Run
Kaspersky WindowsUnlocker to remove Windows system and registry changes made by this virus. It won't take very long.
9. Click on the
Start button once again and fire up the
Kaspersky Rescue Disk utility. First, select
My Update Center tab and press
Start update to get the latest malware definitions. Don't worry if you can't download the updates. Just proceed to the next step.
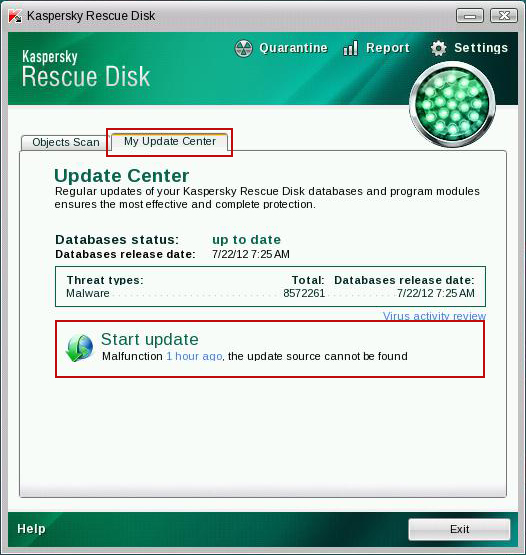
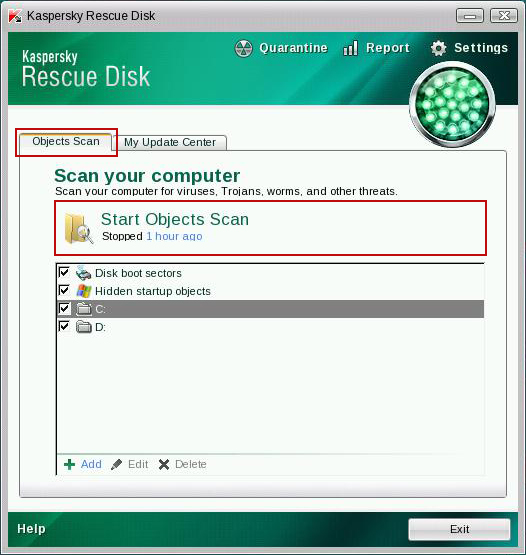
10. Select
Object Scan tab. Place a check mark next to your local drive C:\. If you have two or more local drives make sure to check those as well. Then click
Start Objects Scan to scan your computer for malicious software.
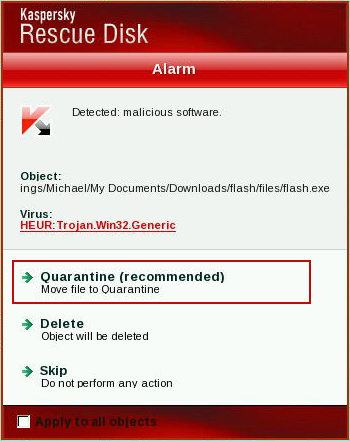
11.
Quarantine (recommended) or
delete every piece of malicious code detected during the system scan.
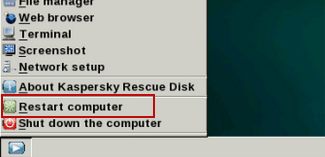
12. You can now close the Kaspersky Rescue Disk utility. Click on the
Start button and select
Restart computer.
13. Please restart your computer into the
normal Windows mode. Download recommended
anti-malware software (direct download) and run a full system scan to remove the remnants of Ukash virus and to protect your computer against these types of threats in the future.