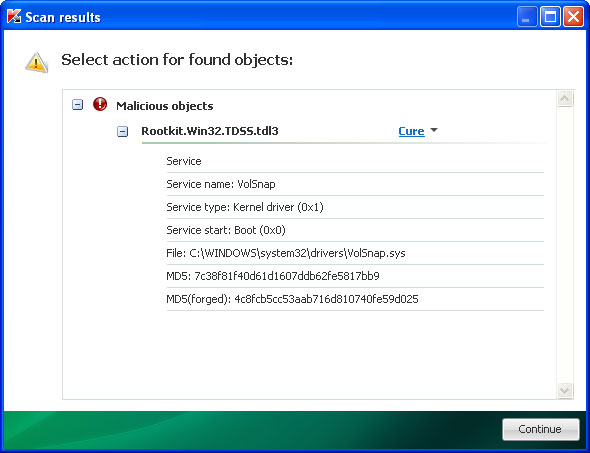
"
METROPOLITAN POLICE"
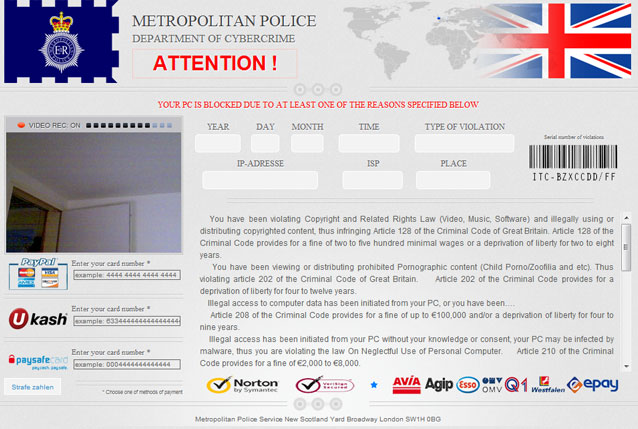
Attention! Illegal activity was revealed! is a ransomware-based malware that demands you to pay up in order to regain control of your computer. About a month ago, we wrote about ransomware that replaces the Windows desktop with a fake warning from the German Federal Police (
BUNDESPOLIZEI). Apparently cybercrooks are moving to Great Britain. As we wrote previously, if your computer is infected with ransomware, you will notice the difference right away. Your Desktop will be taken over by a scam notice headed METROPOLITAN POLICE. It will stop you from accessing your files, programs and system tools. Even if you start your machine in Safe Mode or Safe Mode with Networking you'll get the same issue. The trojan claims that you were watching illegal pornographic websites and states that if you don't pay £75 in 24 hours then your computer will be wiped clean. Don't worry, the Trojan is not capable of doing this. On the other hand, no one would really want to run the risk of losing important files or family photos so there is a great chance that someone will actually fall victim to scam artists behind the Metropolitan Police malware. To remove the METROPOLITAN POLICE ransomware from your computer, please follow the steps in the removal guide below. Good luck and be safe online!


Method 1: Metropolitan Police virus removal instructions using System Restore in Safe Mode with Command Prompt:1.
Unplug your network cable and manually turn your computer off. Reboot your computer is "Safe Mode with Command Prompt". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Command Prompt" and press Enter key.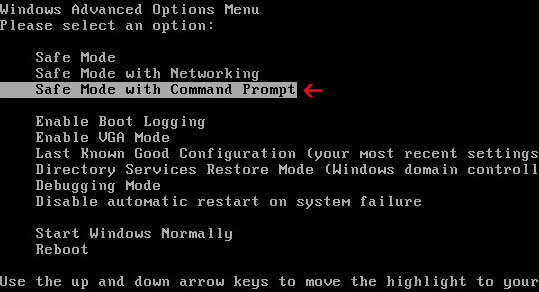
2. Make sure you log in to an account with administrative privileges (login as admin).
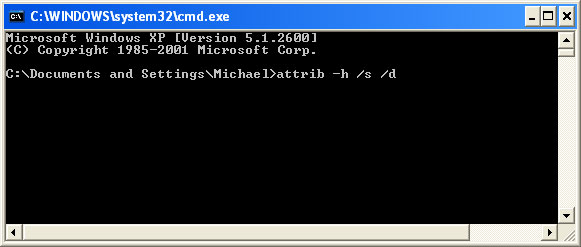
3. Once the Command Prompt appears you have few seconds to type in
explorer and hit Enter. If you fail to do it within 2-3 seconds, the Metropolitan Police ransomware will take over and will not let you type anymore.
4. If you managed to bring up Windows Explorer you can now browse into:
- Win XP: C:\windows\system32\restore\rstrui.exe and press Enter
- Win Vista/Seven: C:\windows\system32\rstrui.exe and press Enter
5. Follow the steps to restore your computer into an earlier day.
6. Download recommended
anti-malware software (direct download) and run a full system scan to remove the remnants of Metropolitan Police virus.
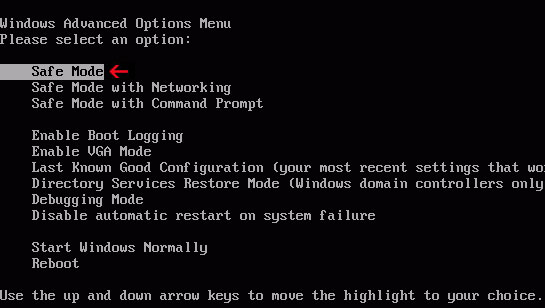
Method 2: Metropolitan Police virus removal instructions using System Restore in Safe Mode:1. Power off and restart your computer. As the computer is booting tap the "
F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "
Safe Mode" and press Enter key.
NOTE:
Login as the same user you were previously logged in with in the normal Windows mode.
2. Once in there, go to
Start menu and search for "
system restore". Or you can browse into the Windows Restore folder and run System Restore utility from there:
- Win XP: C:\windows\system32\restore\rstrui.exe double-click or press Enter
- Win Vista/7/8: C:\windows\system32\rstrui.exe double-click or press Enter
3. Select
Restore to an earlier time or
Restore system files... and continue until you get into the System Restore utility.
4. Select a restore point from well before the Metropolitan Police virus appeared, two weeks should be enough.
5. Restore it. Please note, it can take a long time, so be patient.
6. Once restored, restart your computer and hopefully this time you will be able to login (Start Windows normally).
7. At this point, download recommended
anti-malware software (direct download) and run a full system scan to remove the Metropolitan Police virus.
Method 3: Metropolitan Police virus removal instructions using MSConfig in Safe Mode:1. Power off and restart your computer. As the computer is booting tap the "
F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "
Safe Mode" and press Enter key.

NOTE:
Login as the same user you were previously logged in with in the normal Windows mode.
2. Once in there, go to
Start menu and search for "
msconfig". Launch the application. If you're using Windows XP, go to
Start then select
Run.... Type in "
msconfig" and click OK.
3. Select
Startup tab. Expand
Command column and look for a startup entry that launches randomly named file from %AppData% or %Temp% folders using rundll32.exe. See example below:
C:\Windows\System32\rundll32.exe C:\Users\username\appdata\local\temp\regepqzf.dll,H1N14. Disable the malicious entry and click OK to save changes.
5. Restart your computer. This time Start Windows normally. Hopefully, you won't be prompted with a fake Metropolitan Police screen.
6. Finally, download recommended
anti-malware software (direct download) and run a full system scan to remove the Metropolitan Police virus.
Method 4: Metropolitan Police malware removal instructions in Safe Mode with Command Prompt (requires registry editing):1. Reboot your computer is "
Safe Mode with Command Prompt". As the computer is booting tap the "
F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "
Safe Mode with Command Prompt" and press Enter key. Login as the same user you were previously logged in with in the normal Windows mode.

2. When Windows loads, the Windows command prompt will show up as show in the image below. At the command prompt, type
explorer, and press Enter. Windows Explorer opens. Do not close it.
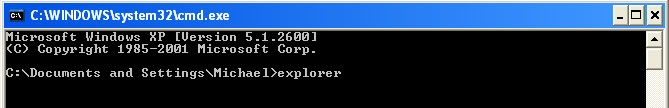
3. Then open the Registry editor using the same Windows command prompt. Type
regedit and press Enter. The Registry Editor opens.
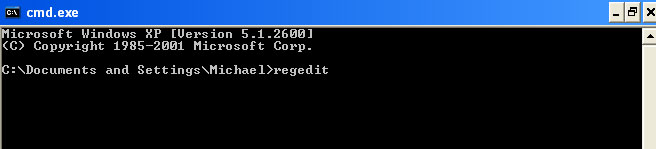
4. Locate the following registry entry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\In the righthand pane select the registry key named
Shell. Right click on this registry key and choose
Modify.
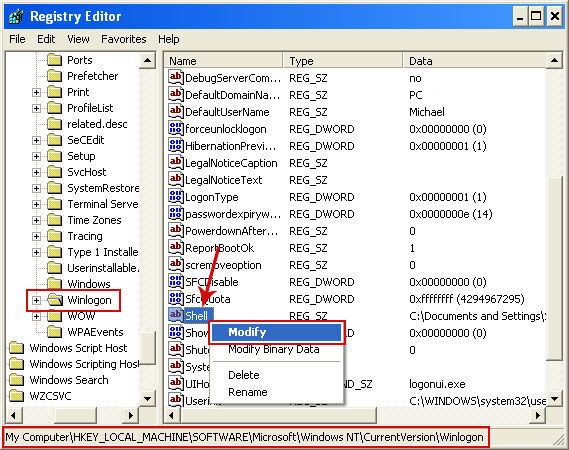
Default value is
Explorer.exe.
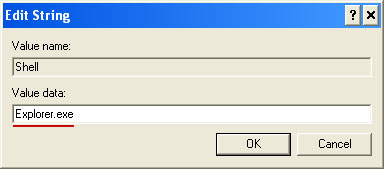
Modified value data points to Trojan Ransomware executable file.
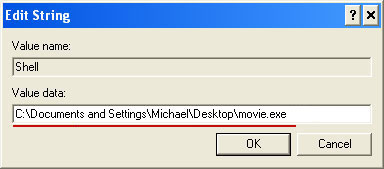
Please copy the location of the executable file it points to into Notepad or otherwise note it and then change value data to
Explorer.exe. Click OK to save your changes and exit the Registry editor.
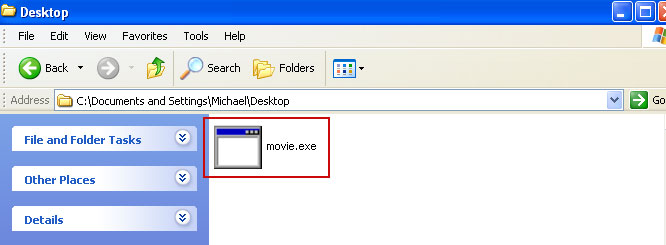
5. Remove the malicous file. Use the file location you saved into Notepad or otherwise noted in step in previous step. In our case, "Metropolitan Police" was run from the Desktop. There was a file called
movie.exe.
Full path: C:\Documents and Settings\Michael\Desktop\movie.exe
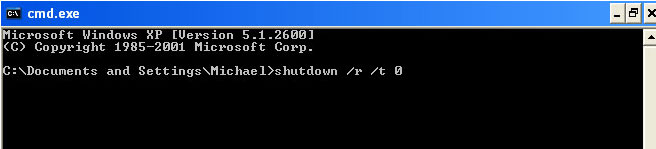
Go back into "
Normal Mode". To restart your computer, at the command prompt, type
shutdown /r /t 0 and press
Enter.
6. Download recommended
anti-malware software (direct download) and run a full system scan to remove the leftovers of this virus from your computer. That's it!
Method 5: Metropolitan Police virus removal using Kaspersky Rescue Disk:1. Download the
Kaspersky Rescue Disk iso image from the Kaspersky Lab server. (
Direct download link)
Please note that this is a large downloaded, so please be patient while it downloads.
2. Record the Kaspersky Rescue Disk iso image to a CD/DVD. You can use any CD/DVD record software you like. If you don't have any, please download and install
ImgBurn. Small download, great software. You won't regret it, we promise.
For demonstration purposes we will use ImgBurn.
So, open up ImgBurn and choose
Write image file to disc.
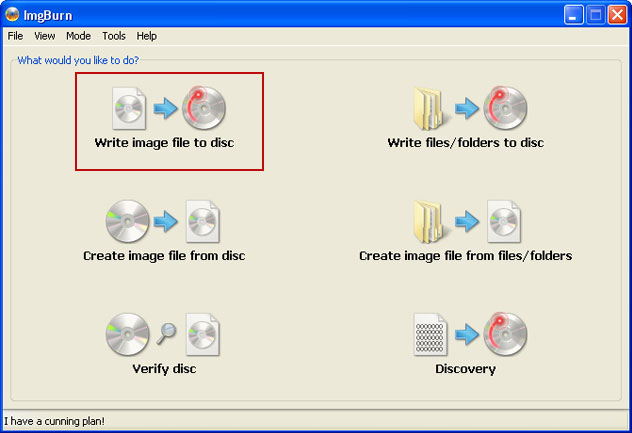
Click on the small
Browse for file icon as show in the image. Browse into your download folder and select
kav_rescue_10.iso as your source file.
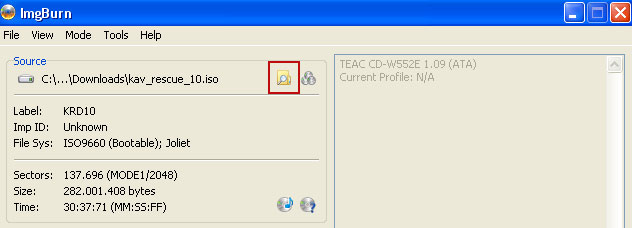
OK, so know we are ready to burn the .iso file. Simply click the
Write image file to disc button below and after a few minutes you will have a bootable Kaspersky Rescue Disk 10.
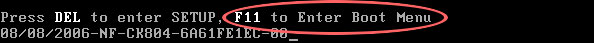
3. Configure your computer to boot from CD/DVD. Use the
Delete or
F2,
F11 keys, to load the
BIOS menu. Normally, the information how to enter the BIOS menu is displayed on the screen at the start of the OS boot.
The keys F1, F8, F10, F12 might be used for some motherboards, as well as the following key combinations:
- Ctrl+Esc
- Ctrl+Ins
- Ctrl+Alt
- Ctrl+Alt+Esc
- Ctrl+Alt+Enter
- Ctrl+Alt+Del
- Ctrl+Alt+Ins
- Ctrl+Alt+S
If you can enter
Boot Menu directly then simply select your CD/DVD-ROM as your
1st boot device.
If you can't enter Boot Menu directly then simply use
Delete key to enter
BIOS menu. Select
Boot from the main BIOS menu and then select
Boot Device Priority.
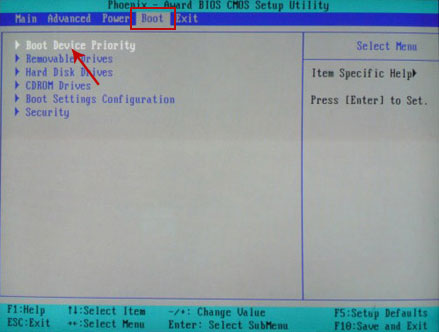
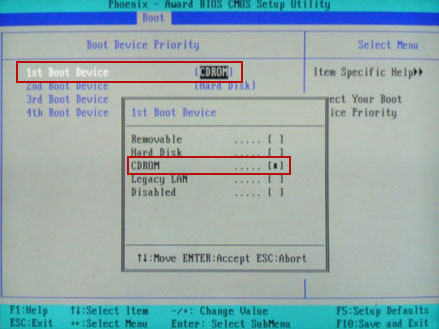
Set CD/DVD-ROM as your
1st Boot Device. Save changes and exist BIOS menu.
4. Let's boot your computer from Kaspersky Rescue Disk.
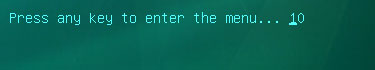
Restart your computer. After restart, a message will appear on the screen:
Press any key to enter the menu. So, press
Enter or any other key to load the Kaspersky Rescue Disk.
5. Select your language and press
Enter to continue.

6. Press
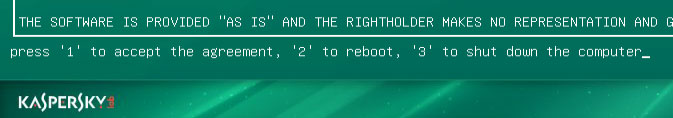
1 to accept the End User License Agreement.
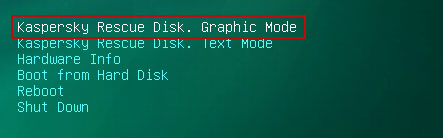
7. Select
Kaspersky Rescue Disk. Graphic Mode as your startup method. Press
Enter. Once the actions described above have been performed, the operating system starts.
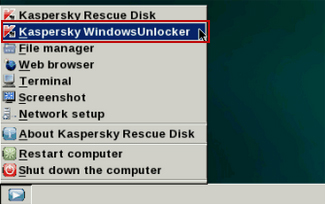
8. Click on the
Start button located in the left bottom corner of the screen. Run
Kaspersky WindowsUnlocker to remove Windows system and registry changes made by Metropolitan Police Virus. It won't take very long.
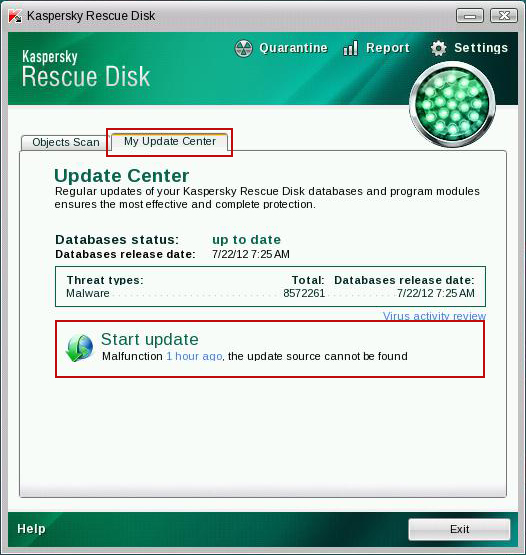
9. Click on the
Start button once again and fire up the
Kaspersky Rescue Disk utility. First, select
My Update Center tab and press
Start update to get the latest malware definitions. Don't worry if you can't download the updates. Just proceed to the next step.
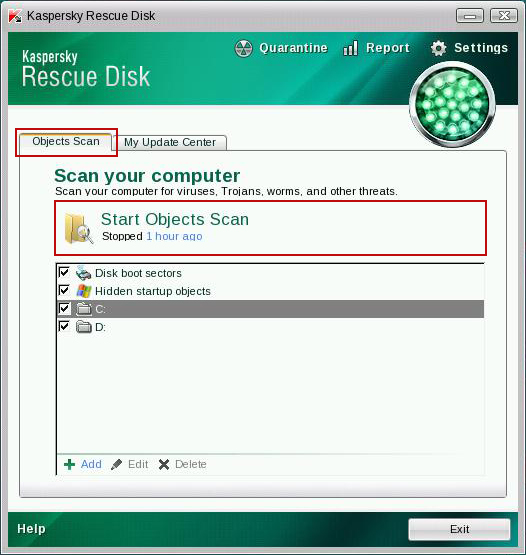
10. Select
Object Scan tab. Place a check mark next to your local drive C:\. If you have two or more local drives make sure to check those as well. Then click
Start Objects Scan to scan your computer for malicious software.
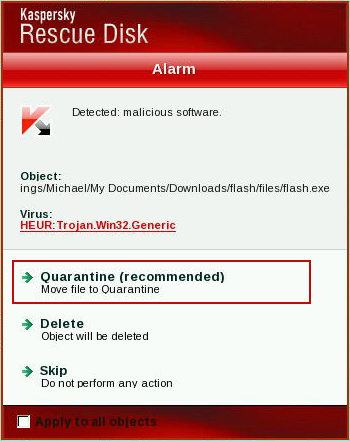
11.
Quarantine (recommended) or
delete every piece of malicious code detected during the system scan.
12. You can now close the Kaspersky Rescue Disk utility. Click on the
Start button and select
Restart computer.
13. Please restart your computer into the
normal Windows mode. Download recommended
anti-malware software (direct download) and run a full system scan to remove the remnants of Metropolitan Police virus and to protect your computer against these types of threats in the future.
Associated Metropolitan Police malware files and registry values:Files:
- [SET OF RANDOM CHARACTERS].exe
Registry values:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\"Shell" = "[SET OF RANDOM CHARACTERS].exe"
Share this information with other people: