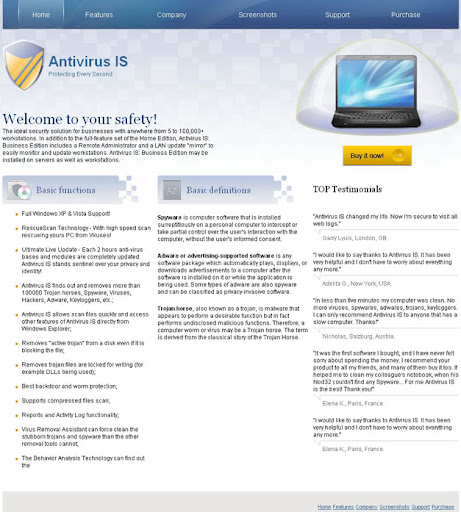
(Thanks to rogueamp)
Once Antivirus8 is installed, it will pretend to scan your computer for malware. Like all the other rogue security programs, it will claim that your computer is infected and that you should purchase the full version of the program to remove found malware and to protect your computer against security threats from the web and emails. What is more, it will constantly display fake security warnings and notifications about active viruses and threats on your computer. Here's how Antivirus8's alert reads:
Antivirus8 Resident Shield: Virus detected
Warning! Active virus detected!
Threat detected: Backdoor.POISON.BQA
This copy of AV is not genuine
Your may be a victim of software counterfeiting. This copy of Antivirus8 is not genuine and is not eligible to receive the full range of upgrades and product support from Microsoft.
Warning! New Virus Detected!
Threat Detected: Email-Worm.Zhelatin


While running, AV8 will block nearly all programs on your computer. It will hijack your web browser and display fake warnings while surfing the web. It could be that you won't be able to download and install any anti-malware software on your computer. In such case, you should reboot your PC in safe mode with networking, download anti-malware software from the list below and run a full system scan. If you can't reboot your computer in safe mode then you will have to download additional tools (i.e. Process Explorer or HijackThis) to end the main process of the rogue program which is av8.exe. Then you should be able to download anti-malware software onto your computer (see removal instructions below). Please note that Antivirus8 may infect system restore points. We strongly recommend you to purge all system restore points and create a new one when the rogue program is completely gone from your computer. If you don't know how to delete system restore points then please follow the steps in the Microsoft knowledgebase article http://support.microsoft.com/kb/310405.
Antivirus8 is from the same family as Antivir 2010 and AntivirusGT. It costs $79.90. If you have already purchased this bogus program then you should contact your credit card company and dispute the charges. If you have any questions or additional information about Antivirus8 please leave a comment. Good luck and be safe online!
UPDATE: Antivirus8 activation code: ABC12-DEF34-GHI56-JKL789. You can use this code to activate Antivirus 8 malware. Please note that in some cases it might not work. Just give it a try. Thanks to serj960 for posting this code.
Antivirus8 removal instructions (in Safe Mode with Networking):
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download free anti-malware software from the list below and run a full system scan.
NOTE: before saving the selected program onto your computer, please rename the installer to iexplore.exe or winlogon.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Antivirus8 removal instructions using HijackThis (in Normal mode):
1. Download iexplore.exe (NOTE: iexplore.exe file is renamed HijackThis tool from TrendMicro).
Launch the iexplore.exe and click "Do a system scan only" button.
If you can't open iexplore.exe file then download explorer.scr and run it.
2. Search for such entry in the scan results:
O4 - HKCU\..\Run: [AV8] C:\Program Files\AV8\av8.exe
Select all similar entries and click once on the "Fix checked" button. Close HijackThis tool.
3. Download free anti-malware software from the list below and run a full system scan.
NOTE: before saving the selected program onto your computer, please rename the installer to iexplore.exe or winlogon.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
4. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Antivirus8 associated files and registry values:
Files:
- C:\Program Files\AV8\
- C:\Program Files\AV8\av8.exe
- C:\Documents and Settings\All Users\Start Menu\AV8\
- C:\Documents and Settings\All Users\Start Menu\AV8\Antivirus8.lnk
- C:\Documents and Settings\All Users\Start Menu\AV8\Uninstall.lnk
- HKEY_CURRENT_USER\Software\A88D52
- HKEY_CURRENT_USER\Software\WinCF
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\explorer.exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "AV8"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\User Agent\Post Platform "WinNT-A8I 23.09.2010"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\explorer.exe "Debugger" = "C:\Program Files\AV8\av8.exe -d"