- Antivirus Vista
- Antivirus Vista 2010
- Vista Antivirus 2010
- Vista Guardian
- Vista Antivirus Pro
- Vista Internet Security
- Vista Internet Security 2010
- Windows Vista 2010
- Total Vista Security
- AntiSpyware Vista
- Vista Security Tool
- Vista Security Tool 2010
- Vista Smart Security
- Vista AntiMalware
- Vista AntiMalware 2010
- Vista AntiSpyware
- Vista AntiSpyware 2010
- Vista Defender
- Vista Defender Pro
- Vista Security

This rogue program is usually distributed through the use of fake online anti-malware scanners, bogus websites and misleading online ads. Once installed, it will be automatically configured to run immediately when Windows starts. When running, it will simulate a system scan and display a variety of infections or threats. However, Vista Antispyware 2010 won't let you remove the infections unless you first purchase the program. Well, that wouldn't be so bad if the threats were real. As we already know, the scan results are false, so why should you pay for it? That's right, you shouldn’t.
When active, Vista Antispyware 2010 will display many fake pop ups and warnings claiming that your computer is compromised. One of the fake alerts reads:
Tracking software found!
Your PC activity is being monitored. Possible spyware infection. Your data security may be compromised. Sensitive data can be stolen. Prevent damage now by completing security scan.
Just ignore such fake warnings. However, the biggest problem is that this scareware blocks legitimate anti-virus and anti-spyware software. And that's not all. It also blocks certain Windows tools and functions in order to protect itself. Last, but not least, it will hijack Internet Explorer. You will be taken to various misleading websites full of false information. What is more, this bogus software will detect perfectly legitimate websites and security threats. Please ignore such information too. Just read the removal guide below and remove Vista Antispyware 2010 from your computer as soon as possible.
Vista Antispyware 2010 removal instructions:
Method #1
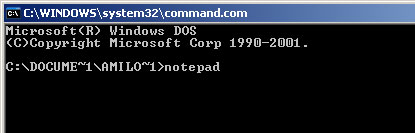
1. Go to Start->Run or press WinKey+R. Type in "command" and press Enter key.

2. In the command prompt window type "notepad". Notepad will come up.

3. Copy all the text in blue color below and paste into Notepad.
Windows Registry Editor Version 5.00
[-HKEY_CURRENT_USER\Software\Classes\.exe]
[-HKEY_CURRENT_USER\Software\Classes\secfile]
[-HKEY_CLASSES_ROOT\secfile]
[-HKEY_CLASSES_ROOT\.exe\shell\open\command]
[HKEY_CLASSES_ROOT\exefile\shell\open\command]
@="\"%1\" %*"
[HKEY_CLASSES_ROOT\.exe]
@="exefile"
"Content Type"="application/x-msdownload"
4. Save file as fix.reg to your Desktop. NOTE: (Save as type: All files)

5. Double-click on fix.reg file to run it. Click "Yes" for Registry Editor prompt window. Then click OK.
6. Download one of the following anti-malware applications:
7. Install the selected application, update it an run a system scan.
8. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Method #2
1. Use another computer and download one of the anti-malware applications listed above (Method #1, step 6),
2. Create fix.reg file as said in Method #1 (steps 1-4). Copy an anti-malware application and fix.reg file to USB flash drive or any other removable device and transfer those files to the infected computer.
3. First of all run the fix.reg file. Then install the anti-malware application, update it and run a full system scan.
4. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
NOTE: after virus removal, if you get an error message saying you need to create an association, then download exefix_vista.reg file and run it. Click "Yes" when prompted. This should fix .exe files association.
Manual removal:
Associated Vista Antispyware 2010 files:
- C:\ProgramData\QJyrk5wvCU1
- C:\Users\All Users\QJyrk5wvCU1
- %UserProfile%\AppData\Local\av.exe
- %UserProfile%\AppData\Local\ave.exe
- %UserProfile%\AppData\Local\QJyrk5wvCU1
- %UserProfile%\AppData\Local\WRblt8464P
- %UserProfile%\AppData\Local\Temp\QJyrk5wvCU1
- %UserProfile%\AppData\Roaming\Microsoft\Windows\Templates\QJyrk5wvCU1
- C:\WINDOWS\Prefetch\AV.EXE-[random].pf
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "%1" %*
- HKEY_CURRENT_USER\Software\Classes\secfile\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "%1" %*
- HKEY_CLASSES_ROOT\.exe\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "%1" %*
- HKEY_CLASSES_ROOT\secfile\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "%1" %*
- HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe" -safe-mode
- HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "C:\Program Files\Internet Explorer\iexplore.exe"
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "%1" %*
- HKEY_CURRENT_USER\Software\Classes\secfile\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "%1" %*
- HKEY_CLASSES_ROOT\.exe\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "%1" %*
- HKEY_CLASSES_ROOT\secfile\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "%1" %*
- HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe" -safe-mode
- HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "C:\Program Files\Internet Explorer\iexplore.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center "AntiVirusOverride" = "1"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center "FirewallOverride" = "1"
Share this information with other people: